BIMI protocol, the industry standard for displaying a branded logo in the mailboxes, gives the senders credibility and the opportunity to rise above others in the already crowded mailboxes. How to implement the BIMI protocol and how it can help email marketing success?
What is BIMI
Historically, significant messages and letters were secured with a wax seal to guarantee sender authentication and trust. Similarly, modern email standard aim to provide the same level of authenticity and trust for email communications.
Google announced on July 21, 2020, that it is starting a pilot program to implement the BIMI protocol in Gmail, joining other major email providers that are beginning to adopt it.
Today, BIMI is becoming the industry standard for displaying a branded logo in subscribers’ mailboxes, as reported by many mailbox providers.
What is BIMI, and why is it so meaningful to anyone who wants to succeed in email marketing?
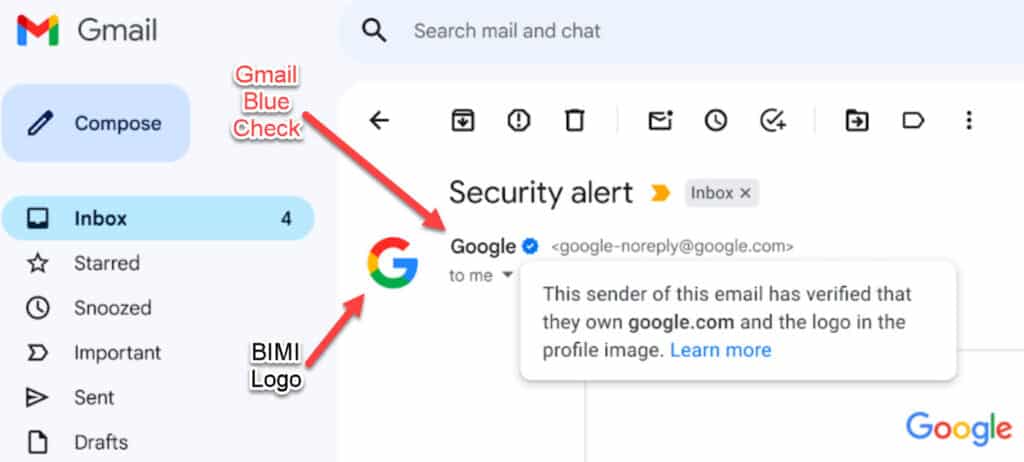
BIMI stands for Brand Indicators for Message Identification – a protocol designed to bring together email security and branding.
Improve email security (I’ll explain why this is important immediately). By improving security, businesses can display their brand logo in the recipients’ inboxes, thus helping recipients identify the sending brand, improving recipients’ engagement, and helping emails to land in the recipient’s inboxes and not to spam.
Unlike other email protocols, BIMI is euniqu because it’s the only security that the end user can actually see with the eye (without digging under the hood).
Currently, some of the logos and images we see in inboxes, are done using a Google account or Microsoft account, and those are not logos in BIMI format.
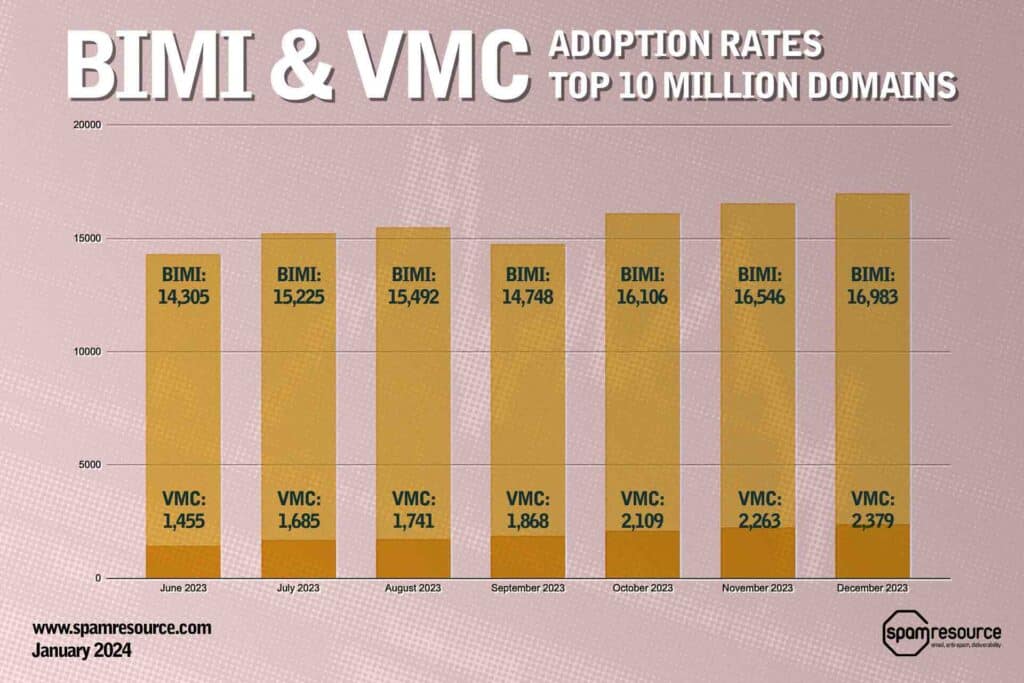
BIMI adoption has become widespread in the past years, and an estimated 500 new branded logos are added each month from the top 10,000 websites. Insecure logo displays, such as Google account images, will be blocked.
In the future, marketers will be able to display a variable logo, for example, a seasonal logo or a general-purpose logo, such as logoes for resterunts.
Note: In the Gmail pilot phase, the pilot will apply to specific marketers.
What do spam and … have in common Vat?
According to monitoring data from Validity, one in six emails will not reach the recipient or will end up in spam. On an annual average, 83% of emails will reach the Inbox, but 7% will be classified as spam and 10% of emails will not arrive at all (bounce for various reasons). Together, that’s 17% (hence the connection to VAT) of your mailing list that goes to hell. This is not fate. Using correct email deliverability practices can help improve inbox reach.
In order to understand the need for email security and clear identification of the sender, we must embark on a short journey of familiarity with the rules of the game of the world of email marketing. SO GO AHEAD – BIMI UP, SCOTTY!
I’ve already linked the crown of “The Last Survivor” to the email. Technology from the 1970s, unlike most contemporary technologies that have long since moved to museums, is growing every year, and all statistics and studies show that email is an effective and critical channel for digital marketing activity about 50 years after the technology was first introduced.
Unlike “ancient” email, modern email is not only a technological means of sending and receiving messages, but a means that requires great skill on the part of the mailing sender (companies and businesses) in order to reach the inbox and not “spam”. As far as the recipient using the email is concerned, a cleaner and clearer email box is received, but on the part of the mailer it is a headache, headache, headache.
About 320 billion emails are sent worldwide every day, but 85% !! Of this huge email traffic is professional spam whose purpose is to sell or act as a kind of “Trojan horse” as a means of introducing malware (malicious code) into organizations in order to fish for information from businesses or people (that’s why this action is called phishing or phishing in Hebrew), to cause disruption or damage (cyber warfare) or to carry out extortion.
Social Engineering
Some of the methods used by spammers are to send emails pretending to be other businesses supposedly on behalf of other legitimate businesses. In some cases, spammers register domain names similar to existing business names only with a different extension (TLD – Top Level Domain) and there are many hundreds of such extensions. Spammers also impersonate existing domains and send messages that appear outwardly authentic, on behalf of existing domains.
Phishing campaigns exist not only by email, but also by telephone (i.e. elderly scams) by sending SMS messages that can be impersonated very easily and even (well, that’s how it started) by regular mail. From old-fashioned chain letters to outright scams.
Quality social engineering campaigns are similar in appearance to real emails sent by real organizations. In many cases it will be messages of a frequent nature that encourage the recipient to act quickly, such as your account has been blocked, click here to release it.
Such malicious actions occur every day and on a huge scale. One of the most recent high-profile examples is Garmin, whose ransomware paralyzed its operations for many days with many millions of customers unable to use their equipment (sports watches that could not upload sports activities to the system, GPS systems for planes and ships that could not receive updates, and more). According to unofficial reports, Grameen paid a huge ransom to the “kidnappers” to resume operations.
It is not common for such a malicious takeover to include leaking the information of customers who switch to trading on the free market and even being used by spammers to attack end customers of organizations that have been attacked.
Prove that you are you, or go to the garbage!
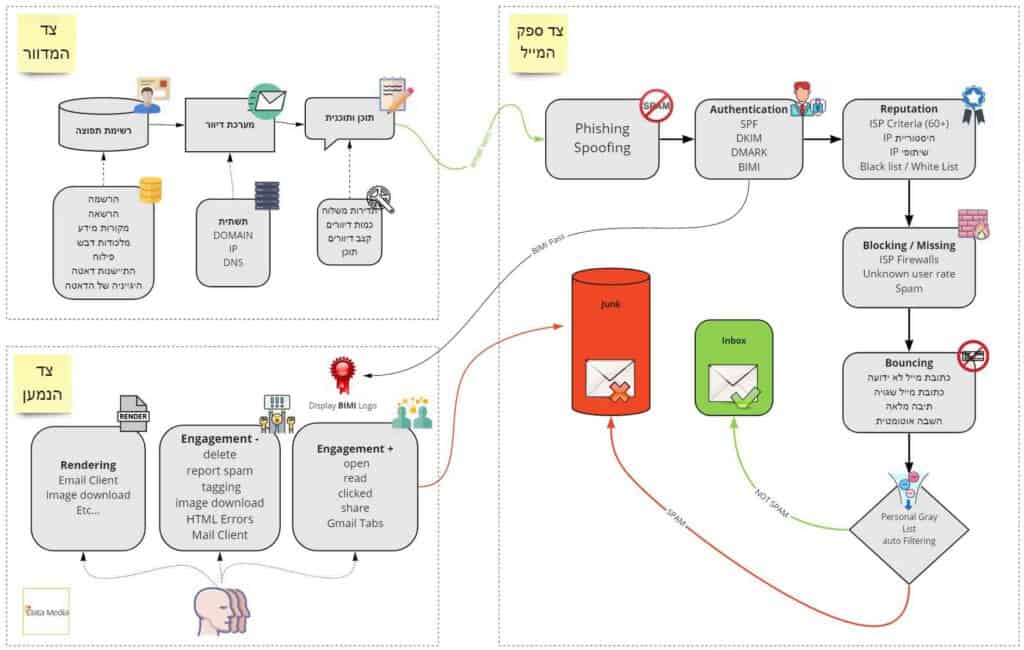
The huge amount of spam and malicious emails has led to the development of filters to identify spam and verify the identity of the sender as authorized to send on behalf of the domain. The major email providers (Yahoo, Gmail, Outlook etc.) and in fact anyone who operates an incoming email server is required to filter spam and viruses using several layers and protective envelopes, otherwise the end users (recipients) will be sorting mail all day long (as mentioned above, 85% of traffic is spam)…
This is how protocols for verifying the sending domain have evolved over the years. From my tests, it is surprising to find that awareness of the existence of these protocols is low or that their implementation is not executed properly, causing companies and businesses that send emails to lose contact with a growing audience due to the fact that their Sender Reputation as a sender is affected in part by these settings.
Protocols:
SPF
The veteran protocol for verifying a sending domain is called SPF – Sender Policy Framework, which every time an email is received, a query is performed and checks the DNS record of the sender domain to make sure that the received email comes from a server authorized to send on behalf of the domain.
Expansion on SPF protocol
DKIM
Another, newer protocol is called DomainKeys Identified Mail (DKIM), which is used to encrypt part of the email when sent using private and public encryption keys. The server receiving each email accesses via a DNS query in order to obtain the public encryption key through which it decrypts the encrypted part of the message and compares it to the visible part of the email. If the content is the same, the sender’s identification was successful and is accepted as a legitimate email. As we will often see, this does not mean that the email will reach the Inbox, it improves the chances that it will not block a phishing attempt and mark the sender as such.
Expansion on the DKIM protocol
DMARC
Domain-based Message Authentication, Reporting and Conformance (DMARC) is a protocol that can be implemented after SPF and DKIM protocols have been implemented (both should be implemented before implementing DMARC), in order to instruct the receiving server what policy it should follow regarding the emails received, in case of discrepancy, in the authentication protocols. In other words, DMARC defines a policy for the receiving server on how to handle emails that it sees as fraudulent attempts (Spoof), who it is supposed to report them to, and how.
DMARC protocol extension
IP Reputation
As part of the fight against spam and weighting the Sender Reputation, not only the sending domain but also the IP address are measured. In most mailing systems, the address is collaborative and is used by many senders, for better or for worse. If the other senders do stupid things it also affects the other IP “partners” and vice versa, good behavior also affects the other sending partners.
I see common Israeli mailing systems that there is no strict monitoring of blocked addresses, which harms senders.
marketeerswho send over a few tens of thousands of emails per month should consider switching to one or more fixed IPs. Working with a static IP address gives the mailer total control over its Sender Score, but presents other challenges related to heating up the IP and constantly monitoring its reputation. It is worth knowing that not all systems allow the assignment of IP addresses to specificmarketeers.
Technical validation, identifying the sending domain and graphical identification by displaying the sender’s logo with the new BIMI protocol are just some of the “rules deliverability ” in order to improve email deliverability.
Expansion on IP heating
The art of getting to your Inbox
Reaching the inbox and not spamming is an art and skill that is closely linked to the reputation the mailer builds for himself. If they said, “A good name is better than good oil,” there are things in Go, even when it comes to electronic mailings. In professional jargon, this reputation is called Sender Reputation, which is like a “grade sheet” formarketeers. The score sheet consists of many parameters. Some of them are technical parameters such as settings and granting correct permissions to the mailing systems to send on behalf of the domain, the reputation of the IP address, and some are elements related to the content, the recipient’s involvement in the content and more.
BIMI – Terms and Conditions
- The BIMI protocol is an additional layer of protection that integrates SPF, DKIM, DMARC. The display of a logo that visually verifies the identity of the sender is possible only if these three are defined as required.
- Good domain reputation.
- Proper implementation of DMARC. In P=quarantine mode or preferably in reject mode.
- PCT=100 in DMARC.
- In Gmail, BIMI implementation during the pilot phase is by invitation only and requires VMC implementation.
- Unfortunately, registering a logo as a trademark is a significant limitation that many businesses will find difficult to implement. The cost to obtain a certificate is still unclear, proof of ownership of a logo trademark is an expensive notarized process similar to registering a trademark (VMC cost is about $1000 per year). According to the BIMI working group, the requirements may change and become more lenient in the future.
- The length of time to obtain VMC approval can take several months, so allowing other entities with a similar trade name is the same as appealing the application.
Note: One of the common mistakes is to run DMARC in p=none mode and leave it that way. While this is the correct initial mode, it is followed by a gradual transition to quarantine mode and finally reject mode.
According to a study by DMA – Data & Marketing Association, the leading reasons recipients report spam is that they don’t recognize the sender. This is also why the BIMI protocol can help reduce spam complaints.
Fake it until you make it
As mentioned, BIMI is suitable for largemarketeers .
Whether marketeers a small mailer or a large marketeers , until you have a BIMI you can display a logo in Gmail by opening a Google account and uploading your logo to the account linked to the sending email address.
אני סלע יפה, מומחה אימייל מרקטינג ועבירוּת אימיילים. אני מזמין אותך לפגישת יעוץ ראשונית של 1/2 שעה ללא עלות בנושא עבירוּת אימיילים ואסטרטגיית אימייל מרקטינג. book an email deliverability discovery call.
Further reading
BIMI Group website
One of the reports about the attack on Grameen
Explanation of the spam industry, Kaspersky

Sella Yoffe
Email Deliverability & Email Marketing Expert
Helping global email senders, startups, digital agencies, and ESPs with email deliverability, email authentication (SPF, DKIM, DMARC, BIMI), and email & content strategy
Podcast creator & Blogger @ CRM.BUZZ & EmailGeeks.Show